-
Posts
226 -
Joined
-
Last visited
-
Days Won
6
Content Type
Profiles
Forums
Events
Everything posted by Meaker
-
Did you do the soldering yourself? What values did you choose for the shunt resistors and did you update the phase count resistor network? Since I've updated my cooling I only get to about 57C at 1900Mhz core clocks during cyberpunk so I'd be interested in re-enforcing the VRM and changing the power limits.
-
See article here: https://www.overclock3d.net/news/cpu_mainboard/a_12-core_ryzen_9_7845hx_mobile_processor_has_been_spotted_-_more_cores_for_future_laptops/1
-
The 4090 is on the ragged edge of scaling, for mobile scaling the TGP back to that point will put it in the efficiency sweet spot. Though the top card should just be a 4070ti mobile in name.
-
Perhaps targeting things like HP workstations? I love the interesting designs like this, I wonder how it would have been in my old 7738G?
-
This is probably some if not the last update to go on it.
-

What have you upgraded on your current laptop(s)?
Meaker replied to Sandy Bridge's topic in Components & Upgrades
-
-
Back together and booting. Good thing I had my skypro around still.
-
Then Prema made a whoops on an update file and I need to manually recover the system. He got me a Lego set to play with effectively 😋
-
Finally got my drain out yesterday but 2 weeks ago I got rapid onset acute appendicitis (went from find to blown in less than 24 hours). I got discharged sooner than the doctors would have liked but I was keen to get out (even though it costs us nothing). Have followed antibiotics etc to the letter and had my checkup yesteday and I seem to be heading for recovery. Have a blood test tomorrow as my course of antibiotics ends just to check it all looks good. Took 10 days of IV antibiotics and a week of oral ones to get rid of it (I hope).
-
Top score was at over 1900Mhz generally so yeah that helps the score!
-
With my power limits and no offset I am getting around 1800Mhz core clocks with peak of 97C hotspot and 80C core. Then I took my cooling off auto and added an offset: This is with a +75Mhz core offset and 1Ghz ram offset 78C max core temp and 95C hot spot. +200/1200 79C/95C.
-

clevo p870km bios question and upgrade to rtx3080 on the way.
Meaker replied to Scruffy's topic in Sager & Clevo
Is this something you are selling? -
Having enough ram is always the first consideration, then comes speed and latency.
-
Make sure you are on a custom or the latest BIOS for the machine. The other TM machines got official support so it will help with driver installs too.
-
Yeah they don't have much of following but have been putting out more stuff and I've enjoyed a lot of it. They have a pocket full of yesterday's out on Spotify.
-

*Official Benchmark Thread* - Post it here or it didn't happen :D
Meaker replied to Mr. Fox's topic in Desktop Hardware
I have the Samsung C32HG70 32" and it's not bad, but a few electrical gremlins 😞 If it has been off for a while I have to unplug it and plug it back in to get it on. It's also got some screen corruption on cold startup now. -
Yeah no river of liquid metal, just a very thin film, widened out a little to get the resistance I want. I was lucky and judged it right first time.
-
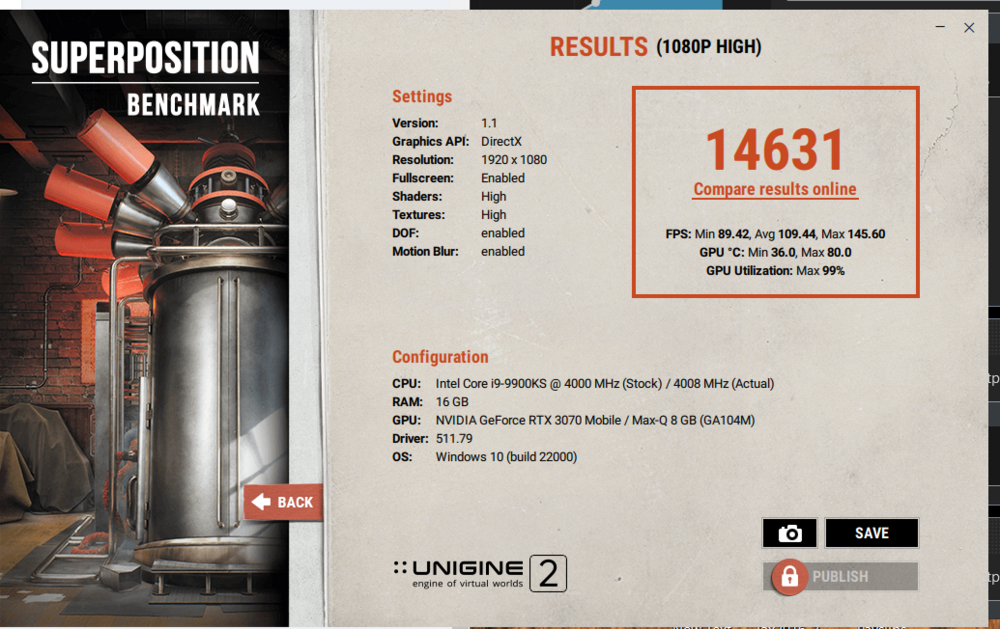
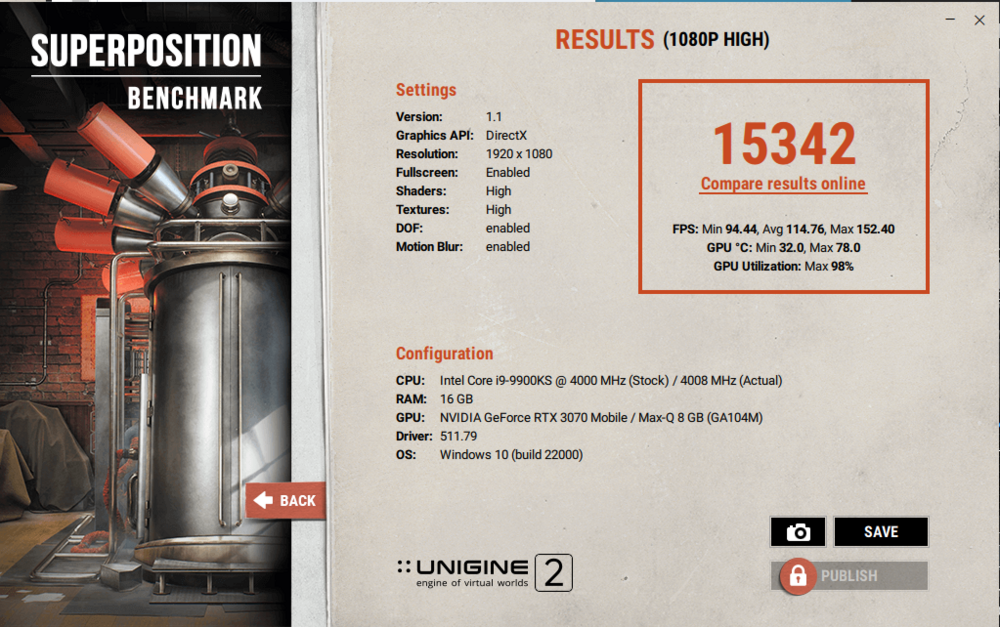
https://www.3dmark.com/fs/26832002 Here you go for performance with it cranked, thanks for the welcome. Yeah I paid over 600 in import vat on the original laptop to the UK. But since it was a business expense I can't complain too much as I saved income tax and national insurance on it.
-
Could not resist this as my first tier X ship:
-

*Official Benchmark Thread* - Post it here or it didn't happen :D
Meaker replied to Mr. Fox's topic in Desktop Hardware
Desktops are so dangerous for me, there was always some new fan, heatsink, GPU or controller I wanted for them. Notebooks made it a lot harder to buy random stuff, also I got bored of desktops a bit after I had done Crossfire 5850 cards in a uATX case with a 1065t at 4Ghz with a seriously overclocked northbridge (and uATX X58 setup with the same GPUs). -
Since my model obviously does not support the boosting function It was something around 120-130W. I've shunt modded it to get that power output increased and the clocks stay around 2Ghz now in heavier titles so it's a 400-500Mhz uplift. I've refined my shunt modding technique, I now immerse the end in liquid metal in a ball at the end of the syringe and then I pull it back. This leaves a skin of liquid metal that's extremely stable.
-
Oh my are there mods, they have upgraded the DX version it runs on even lol.
-
It was from the golden age of space content, I grew on Starlancer (later freelancer) and my favorite ever game: Just watch the intro 🙂